This section of the blog will be about network layouts
Bus Topology
This is an image of the bus topology, it has this name because the main cable in the middle of the diagram looks like a road while the computers connected to the network are like bus stops. For this network to work it does require a main cable and the computers MUST be connected to the main cable. It works by sending a signal to each computer, each computer will then ask the signal (data packet) what computer it is looking for. ( IP address) if it has a different IP address to the data packet it will reject the packet. This method continues until it has reached the correct computer. A main disadvantage to this topology is that if the main cable is broken or cut then the whole network will remain down until it has fixed.
Star Topology
—This is called the
“star network” because the computers are set out like a star. The red dot in the middle is the central
computer and this is what keeps the network going for the other computers. It
is also known as the “host” computer or the network mainframe. —A main advantage to a
Star Topology is that if one cable fails all the computer’s will still be able
to access the network. —A second main
advantage is that you can add a computer to the network without disrupting any
other computers.
This image above is the Mesh Topology, This is a network where each computer and network device is interconnected with one another. this allows most transmissions to the distributed even if one of the connections go down. this topology is not really used for most computer networks as it has a complex infrastructure and can be expensive to set up. A advantage to this network topology is that it has a point to point line configuration which makes identification and isolation of faults easy. another advantage to this network topology is should a network fault occur only those communications between that pair of specific devices will be affected. A massive disadvantage with this network is that it is very expensive to set up.
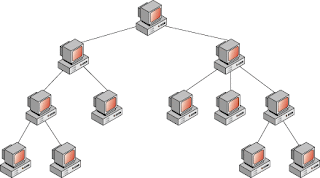
This image above is a Tree Topology. This topology is also refereed to as a star/bus topology. this topology is one of the most common network setups. this tree topology connects multiple start networks with other start networks. some advantages of this topology are expansion of this network is possible and very easy to carry out. Also error detection and correcting that error within the network would also be easy to spot and correct. Some disadvantages include this topology relays on the bus's main cable. So if that cable was to get damaged and break the whole network would go down. Also as more and more segments are added the maintenance of the network topology becomes harder.
The image above shows a server or servers. a server is a computer program that provides a service to other computer programs, and the users. a example of a server is a client server. a client server program awaits and fulfills request from clients. another example of a server is a web server. A web server is the computer program, which is generally housed in a computer that servers requests like HTML pages or files. users can store files and programs onto servers so that all the users within that network can access the data required. Certain permissions can be put into place so that the servers can be secure and keep all data safe. Regular backup of servers is recommended as updating a server may cause it to lose valuable data.
The image above is a diagram of a proxy server and what its purpose is. A proxy server is a server that sits between the user and the internet. this ensures security, and administrative control. the proxy server is associated with part of a gateway server. the proxy server can keep internal webpages (intranet) internal and external webpages external. The user will not be able to tell that the network has a proxy server has it does not advertise its self when in operation.
The image above is a network device called a repeater. The purpose of this network device is to ensure a strong connection running through an Ethernet cable. This is because all Ethernet cables eventually run weaken if the length of the cable is to long. ( about 100 meters . To ensure the cable does not lose strength this repeater is put into place after every 100 meters.
The image above is an example of a network bridge being utilized in a network. The network bridge takes on most of the features of a normal network connection. To configure the network bridge right click the bridge and select proprieties, the user can add or remove connections from and to the bridge. The user is also allowed to enable selected protocols and clients, assign IP address's etc. When a network connection is added the network bridge it loses individual attributes. It no longer has an IP address, clients, protocols etc.
The main reason a network bridge is utilized is to combine two or more local networks, these networks can be wired and wireless into one logical network. this allows all devices to communicate with each other and share data etc.
Ring Topology
The image above is the Ring Topology, —There is no main
cable or host computer they are all as important as each other. It is known as the ring topology mainly because of the fact it looks very much like a ring. each of the five purple dots are the computers and the black line connecting the dots is the wire connecting them to the network. A main disadvantage to this network is that if one of the computers is broken the rest of that ring network will also be broken.
Mesh Topology
This image above is the Mesh Topology, This is a network where each computer and network device is interconnected with one another. this allows most transmissions to the distributed even if one of the connections go down. this topology is not really used for most computer networks as it has a complex infrastructure and can be expensive to set up. A advantage to this network topology is that it has a point to point line configuration which makes identification and isolation of faults easy. another advantage to this network topology is should a network fault occur only those communications between that pair of specific devices will be affected. A massive disadvantage with this network is that it is very expensive to set up.
Tree Topology
Hybrid Topology
A hybrid topology is a selection of two or more typologies are used in one network infrastructure. When two or more topology go into one they do not display the same characteristics of those typologies. it becomes its own topology which is a hybrid network setup. One of the main advantages within this topology is that it is flexible, this means it can be implemented into different environments. adding more devices to these network setups is easy. A disadvantage to this network would be as it is many typologies into one it can be hard to manage the network. also it can be very expensive to expand the network as the infrastructure of this network is a lot more complex then a simple topology.
This next section of the booklet will be all about network devices.
Routers
A router is a small physical device that joins multiple networks together. it is a layer three gateway device which means is connects two or more networks and the router operates at the network layer of the OSI model. when a data packet goes to a router the router reads the address on the data packet which will determine the location the data packet should go.
Switches
The image above is an image of a network device which is called a switch. This is a device that links other network devices. these devices can be computers, printers and servers. a switch serves as a controller enabling network devices to talk to each other efficiently. switches replaced hubs as they are more useful then hubs, an advantage to having a switch in a network infrastructure is that they save the company money as they are cheap and also they are simple to install into a network infrastructure. A main disadvantage with a switch is when handling multiple data packets needs configuration settings to be updated and the design of the network needs to be good, this would take a professional to set up which could cost.
Network interface controller
A network interface controller is also known as a network interface card or a LAN adapter. This is a small piece of hardware that fits into a computer. This hardware component is used to connect a computer to a computer network. The network controller implements the communication between the network and the computer using a Ethernet port. Some network interface controllers work with wired connections while others work with wireless. Ethernet nic's plug into the system bus of the computer and include jacks for network cables while the WiFi nic's contain built in transmitters and receivers which can connect the computer to the network using those transmitters and receivers.
Servers
Proxy
The image above is a diagram of a proxy server and what its purpose is. A proxy server is a server that sits between the user and the internet. this ensures security, and administrative control. the proxy server is associated with part of a gateway server. the proxy server can keep internal webpages (intranet) internal and external webpages external. The user will not be able to tell that the network has a proxy server has it does not advertise its self when in operation.
Repeater
The image above is a network device called a repeater. The purpose of this network device is to ensure a strong connection running through an Ethernet cable. This is because all Ethernet cables eventually run weaken if the length of the cable is to long. ( about 100 meters . To ensure the cable does not lose strength this repeater is put into place after every 100 meters.
Bridge
The image above is an example of a network bridge being utilized in a network. The network bridge takes on most of the features of a normal network connection. To configure the network bridge right click the bridge and select proprieties, the user can add or remove connections from and to the bridge. The user is also allowed to enable selected protocols and clients, assign IP address's etc. When a network connection is added the network bridge it loses individual attributes. It no longer has an IP address, clients, protocols etc.
The main reason a network bridge is utilized is to combine two or more local networks, these networks can be wired and wireless into one logical network. this allows all devices to communicate with each other and share data etc.
This section of the booklet will now be about protocols
TCP/IP Protocol
TCP/IP is a two layered program; it has the higher layer
which is called the transmission control protocol. This protocol is responsible for getting bits
of data in one program in one computer to another program into another
computer. So this is preparing this data
packet to be sent from one computer to another.
The internet protocol is the second layer. This handles the
address part of the delivery, so this packet will reach the correct
destination. TCP/IP is used in computers all
over the world and it is used to prepare the data to be sent. This is important
because without this then the computer would not know where to send the packet.
This is because the internet protocol is responsible for finding the other
computers destination and without this protocol then this process will not take
place. Without these protocols then the
data would not be able to sent, this is because the OSI model uses these
protocols to follow the set of rules on how to send the data.
SNMP protocol
The SNMP protocol stands for the simple network management protocol, this is a internet standard protocol which is used to manage devices on IP networks. the device has to support this protocol for the protocol to work. Devices that support this protocol include routers,switches,servers,printers,modem racks and so on. SNMP is generally used in network management systems to monitor network attached devices for stuff that may need to attention of the administrator. The advantage of this is that if multiple computers need the administrators attention, they can use this to speed up the process so that the administrator can fix problems quickly and efficiently.
IPv4 protocol
The IPv4 protocol is the primary network protocol used with the internet. it was developed in the 1970's and used so that each computer could have a unique address on the internet. It works very similar to a house address. If a user wants to send one data packet to an other user on the internet they would use this protocol to find that user and send the data. IP supports unique addressing for computers on a network. Most networks use the protocol version IPv4 standard that features IP addressing four bytes (32 bits) in length. the newest internet protocol is version 6 (IPv6) and I will explain that below.
IPv6 protocol
The IPv6 standard features address 16 bytes (128 bits) in length. This protocol is used for the same reason as the above. The reason for creating an updated version of the previous protocol is because the IPv4 IP address is meant to be unique, as it is only 4 bytes and (32 bits) in length they are running out of IP address for the new demand of users. The newer protocol is longer in length and will not need an upgraded version of this protocol for some time.
DNS
DNS stands for domain name system. This is used to assign all web address's with names. All web page's on the internet have a unique address, and these address's are based numerically. As people find it easier to remember names of webpages rather then numbers this DNS is put into place. for example, a web page will actually be a set of numbers. When the user types the address into the URL bar it goes to a DNS server. the server then looks for that name and translates that name into the address required to visit the webpage. after the server has converted the name into the address the user can view the webpage.
ARP
The ARP protocol is actually short for Address Resolution Protocol. This is a network layer protocol which is used to convert IP address's into a physical address, such as a Ethernet address. A host that wants to get a physical address will broadcast a ARP request onto the network. The host on the network that has the IP address in the request then replies with its hardware address. There is also another protocol called a reverse ARP (RARP) which can be used by a host to find out its IP address.
IPX
The IPX protocol is short for Internetwork Packet Exchange. This is a networking protocol used to connect networks based on Novell's Netware. Netware is a computer operating system. IPX is connectionless, which means it does not require connections to be maintained during an exchange of packets. it can just be picked up where it left off when a connection is temporarily dropped. IPX used to be used a lot in video games for when they where online. However is was not very reliable so now most video games use TCP/IP which allows long distance gaming.
This next selection of the booklet will be on Network Operating systems ( O/S )
Windows Server 2008
The first network operating system I am going to be talking about is Windows server 2008. This is the newer version of windows server 2003 and this version actually supports 128-bit IPv6 addressing for the internet, and drive encryption. windows server 2008 has added a lot more security, network and administration enhancements compared to the old 2003 version.
Windows server 2008 is built on the windows NT 6.0 kernel which is the same base code as windows vista. Therefor it shares much of the same architecture and functionality of windows vista. The windows server operating systems are built to maintain and manage servers and not to be used for general use. They would be unstable and unreliable.
Windows server 2008 is built on the windows NT 6.0 kernel which is the same base code as windows vista. Therefor it shares much of the same architecture and functionality of windows vista. The windows server operating systems are built to maintain and manage servers and not to be used for general use. They would be unstable and unreliable.
Linux Mandriva
Linux Mandriva is a operating system that can be used to run a server on, it is a open source operating system that is continually being changed and updated. The operating system is free to download and free to use, this is a majour advantage as it cost's to buy windows server and some users would like the fact this operating system is free.more advantages for this operating system includes it can be ran and evaluated from a CD. The operating system also has a enhanced mobile device synchronization, and a very good support club and community online. some disadvantages to this operating system include, installation problems. Some users can find it complicated to install. Another major disadvantage is the user much have some knowledge of Linux. The operating system assumes this and it can be very hard to operate if the user has never used Linux before.
Novell Netware operating system
Novell netware is a network operating system. it is used for multi tasking and to run various services on a personal computer. this operating system would run on a local area network, netware is a software product that runs on lots of different LANS ( local area network). the networks can run from Ethernet or token-ring networks, it provides users and programmers with a consistent interface that is independent of the actual hardware and used to transmit messages within the network.
Novell Netware operating system
Novell netware is a network operating system. it is used for multi tasking and to run various services on a personal computer. this operating system would run on a local area network, netware is a software product that runs on lots of different LANS ( local area network). the networks can run from Ethernet or token-ring networks, it provides users and programmers with a consistent interface that is independent of the actual hardware and used to transmit messages within the network.